Types Of Password Attacks And Prevention Techniques
There are various kinds of cyberattacks in the digital world, and one of the most common types is Password attacks. Both enterprise and individual users have been affected by password attacks across the globe, at one time or another.
A password attack is when the credentials, which include a password, have been compromised, and the attacker gains unauthorized access to the user’s account. Password attacks can be carried out for financial gain, information theft, impersonation, and many other malicious uses.
That said, the types of password attacks have also been categorized depending on how they are carried out. In this post, you shall learn everything there is to know about all sorts of password attacks.
What is a password attack?
In a password attack, the attacker uses a compromised password to gain access to the target’s account. The password can either be known to the attacker beforehand or could use automatic tools to speed up guessing or cracking a password.
The attacker can use different methods to ask the user for their credentials with false pretenses, or use other methods to attain them, such as social engineering, phishing, or keylogging. Once they have your password, obtaining the associated username wouldn’t be a problem, if they do not have it already.
Many applications, accounts, and devices use passwords and PINs to authenticate a user. However, passwords are now considered a weak security protocol to protect critical and sensitive information, since the technology to crack them is advancing at an alarming rate. According to Home Security Heroes, it now takes attackers only 7 hours to crack an 8-character long password that has numbers, upper and lowercase letters, and symbols.
That said, there are various types of password attacks which are defined by how they are carried out. There are 8 types of password attacks:
- Phishing
- Brute-Force attacks
- Dictionary attacks
- Keylogging
- Credential Stuffing
- Password Spraying
- Man-in-the-Middle attacks
- Rainbow Table attacks
Note that some of these password attack types fall into one another’s categories as well. For example, a Dictionary attack and a Password Spraying attack is also a kind of brute-force attack. This is discussed in detail below.
 Types of Password Attacks
Types of Password Attacks
Phishing attacks
Phishing is when an attacker tries to obtain your credentials through fraudulent emails and other social engineering techniques. For example, they might send you an email impersonating a bank or a website and asking you to click on a website link, that looks very much like the original website, and enter your sensitive information. This way, your credentials will be stolen by the attacker.
With phishing attacks, you can normally spot such content with significant training. For example, you might receive an email from “www.itechtics.com.” But if you look closely, you’ll notice that the email is actually from “www.itchtics.com.” Slight typos and mismatching information are quite common in phishing emails, but someone who is inattentive may fall victim to it.
How phishing attackers victimize targets
An attacker can use multiple means of delivering malicious links to the target users. Here are some examples:
DNS Poisoning
The targets are redirected to a malicious URL that looks a lot like the original URL after the Domain Name Server (DNS) server has been corrupted by the attackers.
URL Hijacking/Typosquatting
The attacker creates a website similar to a legitimate website and then sets the domain name which is very close to the original one. The attackers then wait for the targets to make typing mistakes and fall into their trap.
Tabnabbing
Unattended browser tabs are hijacked by the attacker and replaced with malicious websites that imitate trustworthy web pages.
UI redressing/iFrame overlay
The attacker covers a real, clickable button with a link to a malicious page by using transparent layers.
Clone Phishing
Here, the attacker sends a copy of a legitimate email, but instead of legitimate URLs and links, they are replaced with links to malicious websites.
Types of phishing attacks
There are different types of phishing techniques adopted by the attackers:
(Simple) Phishing
In regular phishing, you get a random email from an attacker asking you to reset your password, provide sensitive information to unblock an account, or impersonate a famous person. If you fall victim to such emails and provide sensitive information, they will end with the attacker.
Spear Phishing
Spear phishing refers to dedicated and targeted phishing techniques. In such an attack, you are singled out by the attacker in an attempt to steal your information. Here, the attacker could pretend to be your friend, a relative, or whoever you may know. Such emails usually include brief sentences to look legitimate, asking you to click or download something.
Such attacks are usually carried out by someone who already has access to your circle.
Smishing or Vishing
Smishing is when you receive a fraudulent SMS, and Vishing is when you receive a similar phone call. In these communication methods, the attacker pretends to be a legitimate vendor or person and informs you that your accounts are facing issues, or have been suspended, and therefore need your sensitive information to keep using them.
Whaling
Whaling is when an email that claims to be from a senior member of your firm is sent to you or your organization. You end up providing sensitive information to the attacker, which could have been avoided if you exercised your due diligence to verify the email’s authenticity.
How phishing attacks work
Regardless of how the attacker approached you for a phishing attack, or what type of phishing attack it was, all phishing attacks work in the same manner, more or less.
All phishing attacks usually work by the attacker approaching the target via email or another method, like DNS poisoning. In a phishing attack, the attacker must somehow guide the target’s traffic to end up on a malicious website or web page. This can be done by either sending them a link to a malicious web page, using a transparent layer over a legitimate button on a website, or relying on the chance of the target making a typo whilst entering a URL.
Once the target is on the malicious page, to them, it may seem like a normal and legitimate page, since the attacker designed it that way. Here, the target will enter their credentials onto the false page, and they will end up with the attacker.
Now that the attacker has what they need, the users are then again redirected to the official and legitimate website (which they mimicked) where they continue to perform their tasks as if nothing ever happened.
How to prevent phishing attacks
Anyone can become a victim of phishing attacks. Therefore, you must take multiple measures to avoid becoming their victim. Whether you are a home user or part of an organization, here is everything that you can do to minimize the risk of phishing attacks:
Use anti-phishing software
Nowadays, multiple reputable services offer anti-phishing software and solutions, like SafeUGM NGFW and OPSWAT Email Security, that you can use to mitigate phishing emails from reaching the targets in the first place. If the emails don’t arrive in the inboxes, there won’t be a chance for the targets to accidentally fall prey to such activities.
Of course, this solution applies to enterprise users as such solutions are costly, and usually managed for multiple users.
Have the proper training
This applies to both home and enterprise users. Every individual must have the basic training to keep a lookout for phishing scams. Not only should they be trained to detect and avoid them, but also properly report them to security professionals (in organizations) so that similar emails can be blocked in the future.
Users should be trained to spot the differences between a truly legitimate email and a spam email. This includes keeping a sharp eye on certain elements, like who the email comes from, what is the email address, whether there are any typos, etc.
Other advanced determination factors include noticing the writing styles – does it match the style of the person who usually sends you emails, or is something off?
Don’t click everything you see
Even if you have accidentally opened a malicious email, your device doesn’t need to be compromised (yet). However, clicking a malicious link, or downloading a malicious file will definitely do the trick.
If you suspect that it is a phishing email, do not click any link or button, and do not download any attachments.
Don’t give out sensitive information
Sensitive information should be kept private unless absolutely necessary. Even information like your birthday, pet’s name, etc., should be kept confidential as it can be used to provide answers to security information which leads to resetting your password.
Change passwords regularly
Passwords are prone to getting leaked. Therefore, even in the case that your password has been determined or leaked, changing a password regularly will ensure that even a known password will be of no use.
Use only secure websites
Websites that are unsecured do not have a padlock icon in the address bar, and don’t start with “HTTPS.” Unsecure websites can be hacked into and thus, your passwords and other data can easily be compromised. On the other hand, websites with SSL certificates, that start with “HTTPS”, are more secure.
Adopting the prevention methods above will help reduce the risk of falling into phishing attacks. However, it will not mean that your devices are completely secure from malicious threats. With advancing technologies, attackers are also becoming aware of these mitigation techniques and are finding ways of working around them.
Brute Force attacks
In a brute force attack, an attacker uses the hit-and-trial method to guess and crack a password, encryption keys, or any login credentials, including the usernames. Although this technique has been around for decades, it is still popular within the hacker community as it is still effective.
The objective of a brute force attack is to gain unauthorized access into a user account to further perform malicious activities, such as stealing valuable information, benefit by placing malicious ads on websites, rerouting legitimate web traffic from legitimate websites to malicious ones, and such.
Since there are many combinations for an attacker to try out, alongside any number of usernames, brute force attacks are usually aided with additional computing power and specialized tools, like John the Ripper, that help the attackers try out millions of combinations in a matter of seconds.
Moreover, brute force attacks have different types that are segregated by the approach the attacker takes to perform the brute force attack.
Types of Brute Force attacks
 Types of Brute Force Attacks
Types of Brute Force Attacks
Plain Brute Force attacks
It is considered a simple brute force attack when an attacker attempts to guess the user password or the username without using additional help, like specialized software. The username and password guessing is done manually, and thus, the attacker is only able to try out a handful of guesses.
These simple brute force attacks normally work because people tend to use uncomplex and common passwords, like “password123” etc. Poor password etiquette often leads to the user being hacked, even by the simplest of attacks.
Dictionary attacks
Dictionary attacks are directly a kind of password attack, where the attackers make use of the common words that could be found in a dictionary. A more advanced form of a dictionary attack is where the attackers combine multiple words from the dictionary and manipulate them in an attempt to crack the password.
Hybrid Brute Force attacks
As the name suggests, a hybrid brute force attack is a combination of a plain brute force attack and a dictionary attack. In a hybrid attack, the attacker already knows the username and then continues to manually enter word combinations from the dictionary to guess the login information.
Starting with a list of possible passwords, the attacker tries various characters, letters, and number combinations until they guess the correct one. Hackers can use this method to guess passwords like “California123” or “Cruiser2023” which combine well-known or often-used nouns with numbers, years, or random characters.
Reverse Brute Force attack
In a reverse brute force attack, the attacker already knows a password but doesn’t which username it goes with. Thus, they use hit-and-trial to match a username with the password that they already know.
Typically, the password is known through a previous attack or network breach. Then, the attacker tries to use that information to their advantage and break into the user account.
Credential Stuffing
Credential stuffing is when an attacker uses previously known and compromised passwords on other usernames in an attempt to guess them. This way, they rely on poor password practices in the hope that multiple users are using the same password.
In today’s world, credential stuffing works profoundly as the users still use poor and guess-able passwords.
Password Spraying
Password spraying is a type of brute-force attack where the attacker uses specialized tools to guess the password of a user account using commonly used passwords. However, the salient feature of a spray attack is that it targets multiple user accounts simultaneously. When we say “multiple,” we mean thousands and millions of accounts.
Password spraying attacks reduce the chances of the attacker getting caught with account lockout policies.
Brute Force Attack benefits for attackers
Although it might be obvious, brute force attacks serve a purpose not everyone can comprehend. Here are a few reasons why an attacker may perform a brute-force attack:
Steal personal and sensitive information
An attacker might want to gain sensitive information on the user. They can then use that information to blackmail the user or sell it to the highest bidder.
Spread malware
It may be possible that the brute force attack is nothing personal – the attacker wants to use your account to compromise more users. For example, an attacker might compromise your account credentials to gain access to a website, and then manipulate that website to perform cross-site scripting attacks.
Hijack systems
Sometimes a brute force attack is one of the initial steps in the attack. After the attacker has access to your credentials, they can use it to compromise the entire system. Normally, attackers plant bots to create a botnet, which can then later be used to perform DDoS attacks.
Damage reputation
As we have learned from the past, some brute force attacks are simply carried out to damage an organization’s reputation. The stolen data may not be as valuable, however, the word coming out that a certain reputable company’s data has been stolen will certainly degrade its reputation.
An attacker can carry out a brute force attack for any of the above-mentioned reasons.
Tools for Brute Force attacks
As we mentioned earlier, there are millions of possible combinations that the attacker tries out in a matter of seconds when performing a brute-force attack. This is done with the aid of some powerful attack tools. Performing attacks with these tools requires high computing power, and therefore, some tools are even capable of combining both the CPU and the GPU computing power for effective cracking improvement.
Most of the common tools for brute force attacks are Linux-based, but some are also available for other platforms, including Windows and Android. Here is a list of the common tools used for brute force attacks:
How brute force attacks work
The theory behind a brute force attack is a guessing game. An attack can be totally random guesses, or calculated guesses to guess a username, a password, or both, for a system, a website, or any other platform.
Normally, attackers prefer performing calculated guesses, so it doesn’t waste any time or system resources. Moreover, when they perform a brute force attack, they either know the username they want to target, or the password and a list of potential usernames that they want to try.
Normally, an attacker accesses a system or a website remotely, after which they attempt to use their tools and execute an attack. The software then runs millions of possible combinations to see which one works to log in. Some tools also use a long, compiled list of passwords, that are available on the internet, and quickly go through those passwords in an attempt to crack the credentials.
How to protect against brute force attacks
Brute force attacks are simple and common to execute. Yet, many people fall victim to these attacks. There are several things you can do to protect your accounts and systems against brute force attacks:
Restrict physical access
The first security block is always physical. You must ensure that the system(s) you want to protect can only be accessed (physically) by authorized personnel. If a potential attacker has physical access to the system, they can do a lot worse than a brute-force attack.
Use tokens
Toens, or passkey, are a relatively new form of authentication. Security tokens are issued to the user which authenticates that they are who they say they are. This way, the actual password is removed from the equations, and therefore, there are fewer chances of a break-in.
A passkey is created for an application or website that requires credentials for authentication, i.e. a username and password, or something similar. When you generate a passkey on a supported app/website using a supported platform (discussed below) using your device-specific credentials, a digital token is saved locally on your device (that you used to create a passkey).
Passkeys are currently supported on a handful of websites and the Windows OS. Click on the links below to learn how to create and manage passkey:
Enable multi-factor authentication
The two-factor authentication process (2FA), also known as two-step verification or dual-factor authentication, requires users to verify their identity using at least two different methods. This additional authentication method protects your account even if the first layer of credentials has been breached.
Two-factor authentication protects your online account(s) with an additional security layer, which you can bypass. It requires you to pass a verification exam, which only you can do, and only then will it log in to your account. This verification method is accomplished with 2 basic things: a password and something you have (such as your phone).
For instance, if you are logging in to your Microsoft account with 2FA enabled, Microsoft will ask you for an additional security response by either sending you a text on your number or an email on your alternative email address with a one-time code or authenticating it through a dedicated app (Microsoft Authenticator) on your phone.
Multi-factor authentication also disables an automated brute-force attack when the correct password has been guessed, since the attacker cannot proceed any further without the authentication device that you have configured.
To learn how to enable 2FA on different platforms, click on the links below:
Enable Secure-Sign in screen on Windows
The Secure Sign-In screen is the screen you see when you log out of your computer account, or when you boot up a Windows Server computer. It acts as an additional layer of security where you must physically press the CTRL + Alt + DEL key combination on the keyboard that will take you to the lock screen.
The purpose of this screen is to make sure that no software (or malware) can sign into an account without authorization. The key-pressing makes sure that a human is interacting with the computer. If they have the correct credentials, then they can proceed to sign into an account.
In case there is a brute-force force attack, the secure sign-in screen will prevent the attacker from making repeated guesses, especially when using automated tools.
Learn how to enable the secure sign-in screen on Windows.
Implement Account Lockout Policy
The account lockout policy is a Windows policy that lets you manage when your account is locked out. When a computer account is locked out, a user is not allowed to log back in until a certain time has passed. This policy lets you prevent brute force attacks since it will automatically lock out the user account and no action can be performed, once a certain number of incorrect login attempts have been made.
There are several Group Policies that you manage to configure the account lockout policy. Here is what they are and what they do:
- Account lockout duration: The time (in minutes) for when the user will be unable to sign back in, even with the correct credentials.
- Account lockout threshold: Defines how many tries before the Administrator account is locked and no more login attempts are granted.
- Allow Administrator account lockout: Whether the Administrator account will be locked out or not.
- Reset account lockout counter after: Defines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts.
Use the following steps to configure the account lockout policy:
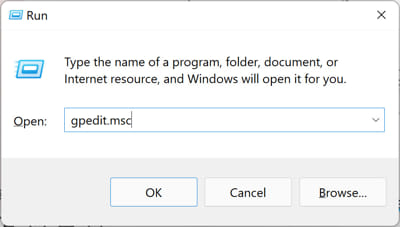
Press the Windows Key + R to open the Run Command box.
Type in “gpedit.msc” and press Enter to open the Group Policy Editor
 Open Group Policy editor
Open Group Policy editorNow navigate to the following from the left pane:
Local Compter Policy >> Computer Configuration >> Windows Settings >> Security Settings >> Account Policies >> Account Lockout Policy
Double-click the policy “Account lockout threshold” in the right pane, and set the number of wrong attempts you want to allow before the Administrator account locks itself.
 Set account lockout threshold
Set account lockout thresholdClick Apply and Ok when done.
Now make sure that the “Allow Administrator account lockout” policy is enabled (default value).
If not, double-click it and Enable it.
Note: If you do not want the Administrator account to lock out but want only the other accounts, then set this policy to Disabled.
 Enable Administrator account lockout
Enable Administrator account lockoutDouble-click “Account lockout duration” and now enter the time you want the Administrator to lock itself for.
 Set time to lock account for
Set time to lock account forClick Apply and Ok.
Now double-click “Reset account lockout counter after” and enter the time you want the threshold counter to reset to 0.
Note: This value should be less than or equal to the value for “Account lockout duration.”
 Set time to reset threshold counter to 0
Set time to reset threshold counter to 0Click Apply and Ok.
Now that all policies have been configured, run the following cmdlet in an elevated Command Prompt to enforce the new policies:
GPUpdate /Force
 Enforce new group policies
Enforce new group policies
Your local Administrator account will now automatically lock itself and deny any login attempts when incorrect login attempts are made that satisfy your policy configurations.
Use strong passwords
Weak and inadequate passwords are easier to breach, as they can be predicted. Normally, brute force attacks use a list of common passwords to try out first. If yours is a common one, the attacker might gain almost instant access. Therefore, make sure that your password is unique. Note that while a random name followed by your birthday may seem unique, it might not. Therefore, do your research before setting a unique password.
Moreover, increase the number of characters in a password. The longer the password, the more difficult it becomes to crack. Additionally, you should also use a variety of characters, including small letters, capital letters, numbers, and special characters.
You should also use password managers. Password managers allow you to store passwords offline, and you can access them with a single, unique, and complex password. Additionally, most password managers also offer additional tools, such as random password generation and password vulnerability tests.
Remove unused accounts
Unused accounts that have been left unmaintained are often the targets of attackers since they do not have updated security protocols. Additionally, no one may notice once it has been compromised. Therefore, it is advised that you regularly remove unused accounts from the system to prevent brute-force attacks.
Password encryption and salting
When saving a password, such as in a password manager, make sure that your password is either encrypted or salted. In both of these methods, the stored password is not the actual password. Rather, it has been manipulated in such a way that only the authentic user knows. Thus, they also know how to remove the extra characters from the password for it to become the real password again.
Use CAPTCHAs
CAPTCHAs are used by websites to prevent unwanted traffic, such as automated scripts and bots, from logging in, signing up, or simply browsing their content, as it increases traffic dramatically and may lead to spamming. To put it simply, it is used to verify that you are a real person to conduct a legitimate online transaction.
If you are a website owner, then you should adopt using CAPTCHAs after a certain number of attempts to block automated brute-force attacks from occurring.
Use denylists
Allowlists allow specific IP addresses to access the system. Similarly, a denylist blocks certain IP addresses. Using denylists, you can block known malicious IP addresses from accessing the system at all. This will prevent any potential brute-force attacks before they even happen.
Keylogger attacks
A keystroke logging, or keylogging attack is a technique where an attacker secretly spies on you by monitoring the keys pressed on your keyboard. While it is considered legal if done correctly under some specific circumstances, it is still illegal to use this technique to spy on a victim’s password.
A keylogger can be considered a password attack when the attacker is watching you type in your password. Regardless of the complexity of your password, an attacker will simply gain access to your account by observing what you entered on your keyboard.
Additionally, since the attacker is already spying on you, they may already know the username as well. Therefore, technically, keylogging isn’t a password-cracking technique, it is a spying technique.
Types of keyloggers
There are different kinds of keyloggers, but all of them have the same purpose; to spy on what you press on the keyboard. The image below lists the different types of keyloggers.
 Types of keyloggers
Types of keyloggers
To learn more about each type of keylogger, read the dedicated section: Types of keyloggers.
How keylogging works
Keylogging requires either hardware or software to be installed on the computer. Although possible, hardware keyloggers are not used very much since they require physical access to the PC by the attacker. Therefore, they prefer using software keyloggers.
Software keyloggers are usually delivered through phishing emails, and intimations to update their software. A gullible user then may click on the malicious link which will plant and execute the keylogger on the system.
Once the keylogger is deployed, all keystrokes are recorded by the program and communicated to the attacker. The attacker can then use this information to gain unauthorized access to websites, extort money from you, or sell your information to the highest bidder.
How to prevent keylogging
Once a keylogger is installed on your computer, it will spy on you and send your data to the attacker, unless proper prevention techniques are not implemented. Therefore, our main goal is not to let the keylogger onto your PC in the first place.
Here are a few things you can do to prevent keylogging attacks:
Man-in-the-middle attacks
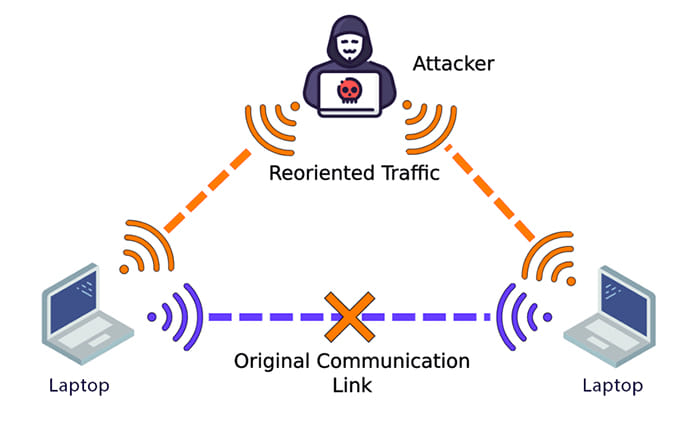 Man-in-the-middle attack
Man-in-the-middle attack
A man-in-the-middle attack is when a third unknown person eavesdrops or has unauthorized access to your information while it is being communicated. For example, if you are attempting to establish an HTTP connection to a server, an attacker might intercept those handshakes and pretend to be the server, while sending back replies to your PC, making it think that the malicious computer is the actual server.
A man-in-the-middle attack can be a password attack if the attack was designed to steal your password, username, or both. For example, an attacker may create a fake web page that looks just like the real one, where you enter your credentials, which are now available to the attacker. The attacker would then redirect you to the official web page without you knowing anything about the attack.
Types of man-in-the-middle attacks
As with most cyberattacks, man-in-the-middle attacks are also of different types which are defined by how the attack was carried out. Here are the different types:
IP Spoofing
Spoofing refers to the modification of something to hide the actual values. In IP Spoofing, the attacker modifies the IP addresses within the data packets to hide the true identity of the sender. For example, they may change the actual IP address of the sender with the IP address of a legitimate server, so that your device may think it is communicating with the actual server it is supposed to.
DNS Spoofing
Similar to IP Spoofing, in Domain Name Server (DNS) Spoofing, the actual values of the DNS are altered to redirect a victim to a false and malicious web page instead of the real one. This is done by making changes in the DNS entries and redirecting the traffic away from the legitimate website and onto the malicious one.
HTTPS Spoofing
The actual HTTPS protocol is encrypted, providing the user with a sense of security. However, in an HTTPS Spoofing attack, a website or a web page only shows that it has an HTTPS connection, but in reality, they have been redirected to an insecure, HTTP-only connection. Since the connection is insecure, the attackers take advantage of it and steal the user’s data.
Email Hijacking
An attacker may gain access to sensitive emails, such as bank emails for financial gains. They can then send out similar emails for fraudulent activities and ask users to wire money into malicious accounts.
Wi-Fi Eavesdropping
Malicious Wi-Fi networks are set up by attackers that are open to use for everyone. They often pretend to be nearby businesses so that they do not gain attention. However, the targets that do connect to such networks are attacked and their sensitive information is compromised.
SSL Hijacking
In an SSL hijacking attack, the attacker exploits a valid online session by gaining access to the session’s ID information. This attack is an extension of an HTTPS spoofing attack.
Session Hijacking
Cookies are used to store personal data, like usernames and passwords, track online activities, etc. Attackers steal these cookies, which contain all your information, and then hijack your online session.
If you look very closely, then all of the above-mentioned attacks are types of man-in-the-middle attacks. This is because the compromise took place by someone spying, or attacking in the middle of an existing session or communication.
Tools for man-in-the-middle attacks
In a typical scenario, man-in-the-middle attacks cannot be performed without the help of specialized tools and utilities, unless they have physical access to the communicating servers and networks. But even then, some tools will be needed.
That being said, attackers use specialized tools to perform man-in-the-middle attacks. Here are some of the common tools being used for such malicious activities:
How man-in-the-middle attacks work
As the name of the attack suggests, an attacker must first place themselves between the victim and the server. Once that is achieved, they then only need to manipulate the data packets to perform their actual agenda of the attack.
An attacker can put themselves between a client and a server through different means, which usually are one of the following:
- Create an unsecured wireless access point in the hopes that the client will connect to it.
- Penetrate a wireless network by cracking the password, possibly through brute force, guessing a weak and common password, or any other means.
- Creating a fake website and redirecting the users to make them think that it is the real deal so that they provide sensitive information directly to the attacker.
- Manipulating the IP protocols and sending out fake emails to get the victims to change their passwords or log into the fraudulent website.
Once an attacker has put themselves in the middle, your data is already compromised to some extent. Now, they take advantage of their position.
Now, the attacker must use specialized tools to receive and decrypt the data packets so that they are human-readable. This is how your sensitive information is stolen through man-in-the-middle attacks.
How to prevent man-in-the-middle attacks
There is no sure-short way of determining whether your communication with a server is being invaded by a third person, at least not with the naked eye. Therefore, you must take some preventive measures to make sure that your communication is not invaded in the first place.
Here are a few ways to prevent man-in-the-middle attacks:
Avoid unsecured websites
The first thing you should avoid is accessing unsecured websites and web pages. Avoid websites with no HTTPS connections as they are more vulnerable to online threats, like cross-site scripting attacks.
Use DNS-over-HTTPS (DoH)
DNS-over-HTTPS is a feature that aims to make web browsing secure by encrypting the communication between the client computer and the DNS server. This will prevent your sessions from being hijacked.
Do not connect to public, unsecured networks
Public Wi-Fi networks that are unsecured with no passwords are often bait for victims. Connecting to such networks can compromise your device, data, and online activity by someone who is connected to the same Wi-Fi.
Network segmentation
Network segmentation is an architectural design that divides a network into multiple sections or subnets, each acting as its own small network. This approach prevents devices of one segment from penetrating the devices in another segment of the network. Of course, this concept in turn reduces the risks of man-in-the-middle attacks.
Encrypt emails
Emails are often the targets of man-in-the-middle attacks. Therefore, it is better to use email encryption services so that they can only be read by authorized individuals.
Use Virtual Private Networks (VPNs)
VPNs are encrypted, virtual tunnels you create for point-to-point communication. VPNs help prevent man-in-the-middle attacks are the data transiting through these tunnels are safe, and the attacker would need a decryption key to penetrate your information.ra
Use endpoint security
Reputable endpoint security solutions are quick in catching fishy content, including malicious websites. Use a reputable endpoint security solution, like BitDefender Total Security, to protect yourself from falling prey to malicious content.
Rainbow Table attacks
Rainbow table attacks are password attacks where the attacker uses pre-calculated tables to decipher passwords.
When you sign up on a website and create a new account, your password is stored on the server after hashing (where the password is mathematically converted to match the corresponding characters). Then when you try to log in, the password is converted into characters again, through hashing, and then matched with the password saved on the server. You are then logged in if the two passwords match.
In a rainbow table attack, the attacker uses tables to hash common passwords in an attempt to log in. In this way, rainbow table attacks are very much similar to Dictionary attacks.
When rainbow table attacks occur
It is not very often that an attacker chooses to perform a rainbow table attack. This attack is only carried out under certain circumstances.
A rainbow table password attack is only beneficial if the attacker gets their hands on a server that contains hashed passwords. If so, the attacker would try to perform a rainbow table attack, together with a brute-force attack, and use tools to try to crack the actual password. Some might consider this reverse-engineering a password, where the plain-text password is extracted from a hashed password.
How to prevent rainbow table attacks
There are several ways to prevent your password from being cracked in a rainbow table attack:
Use strong and unique passwords
Your first line of defense should be using a unique and strong password. A unique password is considered one that no one could guess (something unpredictable). Using names and years may seem like a good idea, but are the most gullible passwords.
Additionally, the longer a password, the more secure it is considered. It takes automated tools only a matter of seconds to crack smaller passwords. However, longer and more complex passwords are more resilient to such tools. They can still be cracked, but it will take a lot longer, and a whole lot more computing resources.
Salting
There is a concept known as “salting” where you add extra characters to a password. For example, salting will convert my typical password, which is “Subhan123”, into a more complex and unique password, which could be “Saubbchdaenf1g2h3”. The password still makes out “Subhan123”, but with additional characters between every letter.
The term “salting” comes from adding salt as seasoning on top of food – adds a bit of flavor.
Avoid old hashing algorithms
Instead of using older hashing algorithms, like MD5 and SHA1, one should adopt using relatively modern algorithms. SHA256 and SHA512 are more modern and more secure than the older hashing algorithms.
Do rehashing and resalting
Above, we mentioned that you should adopt salting to make a password stored on a server more secure. An additional layer of security could be added by salting the hashed password and then rehashing it. This will make rainbow table attacks less effective and more time-consuming.
Adopt passwordless authentication
Passwordless authentication is perhaps the safest of all authentication methods. It does not involve you entering any characters that are saved on any server. The safest of all passwordless methods is using Passkeys, but you can also use other means, such as biometrics, facial recognition, etc. With Passkeys, you use digital tokens instead of passwords as an authentication method.
Closing words
Password attacks are one of the simplest kinds of attacks in the history of cybersecurity. They have been around for decades. Yet, because of our negligence, they are still one of the popular choices for the attackers.
Reusing the same password on every website, and that too, which is not very secure, motivates attackers to use the same techniques in cracking our passwords and gaining unauthorized access. If we want to make our online presence more secure, it is in our best interest that we adopt the prevention methods discussed in this post that will help reduce the risk of falling prey to a password attack.
 Open Group Policy editor
Open Group Policy editor Set account lockout threshold
Set account lockout threshold Enable Administrator account lockout
Enable Administrator account lockout Set time to lock account for
Set time to lock account for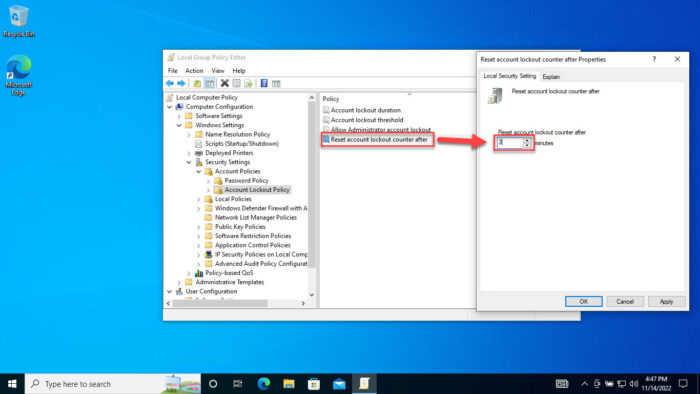 Set time to reset threshold counter to 0
Set time to reset threshold counter to 0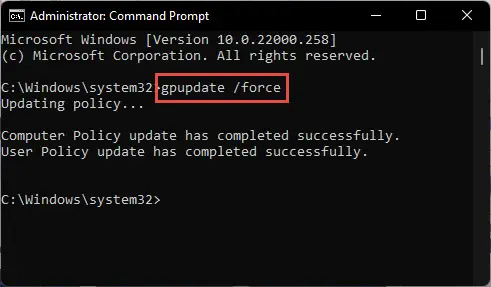 Enforce new group policies
Enforce new group policies